Hot News in All Sections
- Apple Vision Pro: A New Era of Spatial Computing
- How to Find Inner Peace in a Chaotic World: A Powerful Zen Story - The Stillness of the Zen Pond
- Google's New AI Search: A Game-Changer for Online Information
- Shambhavi Mudra: How to Gaze at Your Eyebrows Center and Unlock Your Potential - Part 3
- Will Artificial Intelligence Take Over the World?
- How to Speed Up Your Dell Inspiron 15 3000 Series Laptop for the New Windows 11
Items filtered by date: Thursday, 07 June 2018
The splendid Herrenhausen Gardens of Hanover
VPNFilter - New Router Malware
Systems Affected
The devices include the following vendors:
- Linksys E1200
- Linksys E2500
- Linksys WRVS4400N
- Mikrotik RouterOS for Cloud Core Routers: Versions 1016, 1036, and 1072
- Netgear DGN2200
- Netgear R6400
- Netgear R7000
- Netgear R8000
- Netgear WNR1000
- Netgear WNR2000
- QNAP TS251
- QNAP TS439 Pro
- Other QNAP NAS devices running QTS software
- TP-Link R600VPN
While the above are the currently known routers that can be infected with VPNFilter, there is no guarantee that they are the only ones.
Threat Level: High
Overview
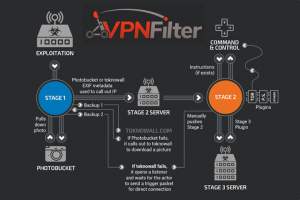
VPNFilter is a malware that targets routers and NAS devices in order to steal files, information, and examine network traffic as it flows through the device. It is a multi-staged piece of malware where Stage 1 makes the connection, Stage 2 delivers the goods, and Stage 3 acts as plugins for Stage 2. These include a packet sniffer for spying on traffic that is routed through the device, including theft of website credentials and monitoring of Modbus SCADA protocols. Another Stage 3 module allows Stage 2 to communicate using Tor."
VPNFilter "is unlike most other IoT threats because it is capable of maintaining a persistent presence on an infected device, even after a reboot,"
Description
When the VPNFilter malware is installed, it will consist of three different stages, with each stage performing specific functions.
Stage 1 is installed first and allows the malware to stay persistent even when the router is rebooted.
Stage 2 allows the attackers execute commands and steal data. This stage also contains a self-destruct ability that essentially makes the router, and thus your network connection, non-functional.
Stage 3 consists of various plugins that can be installed into the malware that allow it to perform different functionality such as sniff the network, monitor SCADA communication, and to communicate over TOR.
While Stage 1 will run again after a router is rebooted, Stage 2 and 3 will not.
Solution/ Workarounds
To completely remove VPNFilter and protect the router from being infected again, the following steps should be followed:
- Reset router to factory defaults
- Upgrade to the latest firmware
- Change the default admin password
- Disable Remote Administration
References
https://www.symantec.com/blogs/threat-intelligence/vpnfilter-iot-malware
https://www.pcmag.com/news/361431/is-your-router-vulnerable-to-vpnfilter-malware
https://www.cert.govt.nz/it-specialists/advisories/advisory/vpnfilter-malware/
Disclaimer
The information provided herein is on "as is" basis, without warranty of any kind.
Does Religion Cause War?
In simple term, Religion is basic set of beliefs concerning the reason, nature, and purpose of the world,
The Technology Video of The Day
Email Newsletter Subscription
Come Join with Our YouTube Channel
Articles Archive
Electrical and Electronic World News, Lessons, Reviews and Articles
- HackRF One: Exploring Real-Life Use Cases of a Powerful Software Defined Radio Device
- USRP Software Defined Radio: The Power and Perils of Building Fake Cell Towers
- Tech Briefs - Digital Magazine - Download Link For Free Copy
- Introduction to SDR-Software Define Radio Dongle Sinhala Video Lesson
- Review on RTL SDR Dongle
- The Complete Basic Electricity and Electronics Course
Phones World News, Lessons, Reviews and Articles
Security World News, Lessons, Reviews and Articles
- Apple's Stealthy Maneuvers in the AI Landscape
- AI Safety Takes Center Stage: Insights from US Congress Members Hearing
- Google's New Passkey Technology: A Game-Changer for Online Security
- Over a Million WordPress Websites Compromised by Balada Injector Malware Campaign
- QuaDream: The Emerging Israeli Spyware Firm and Its Threat to Digital Privacy
Games World News, Lessons, Reviews and Articles
- Soaring to New Heights: The Evolution and Impact of Microsoft Flight Simulator
- The World of Minecraft: Creativity, Community, and Endless Possibilities
- Unleash Your Strategic Mastery: A Guide to Microsoft's Age of Empires III: Definitive Edition
- Hints to Win the FreeFire Mobile Game
- Free Fire The Best Mobile Game in 2022















 Please wait...
Please wait...